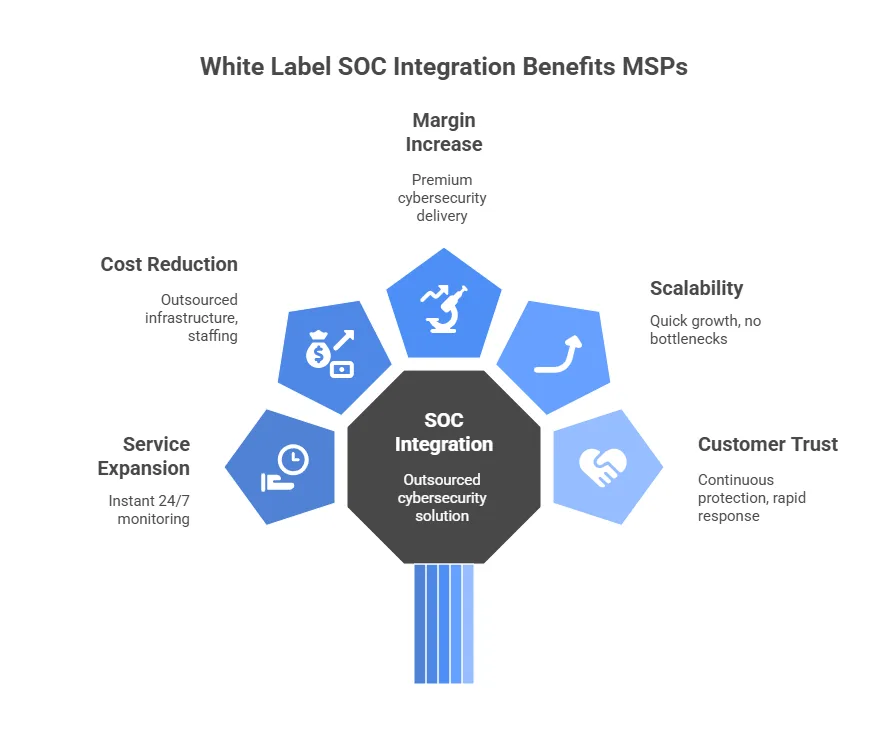
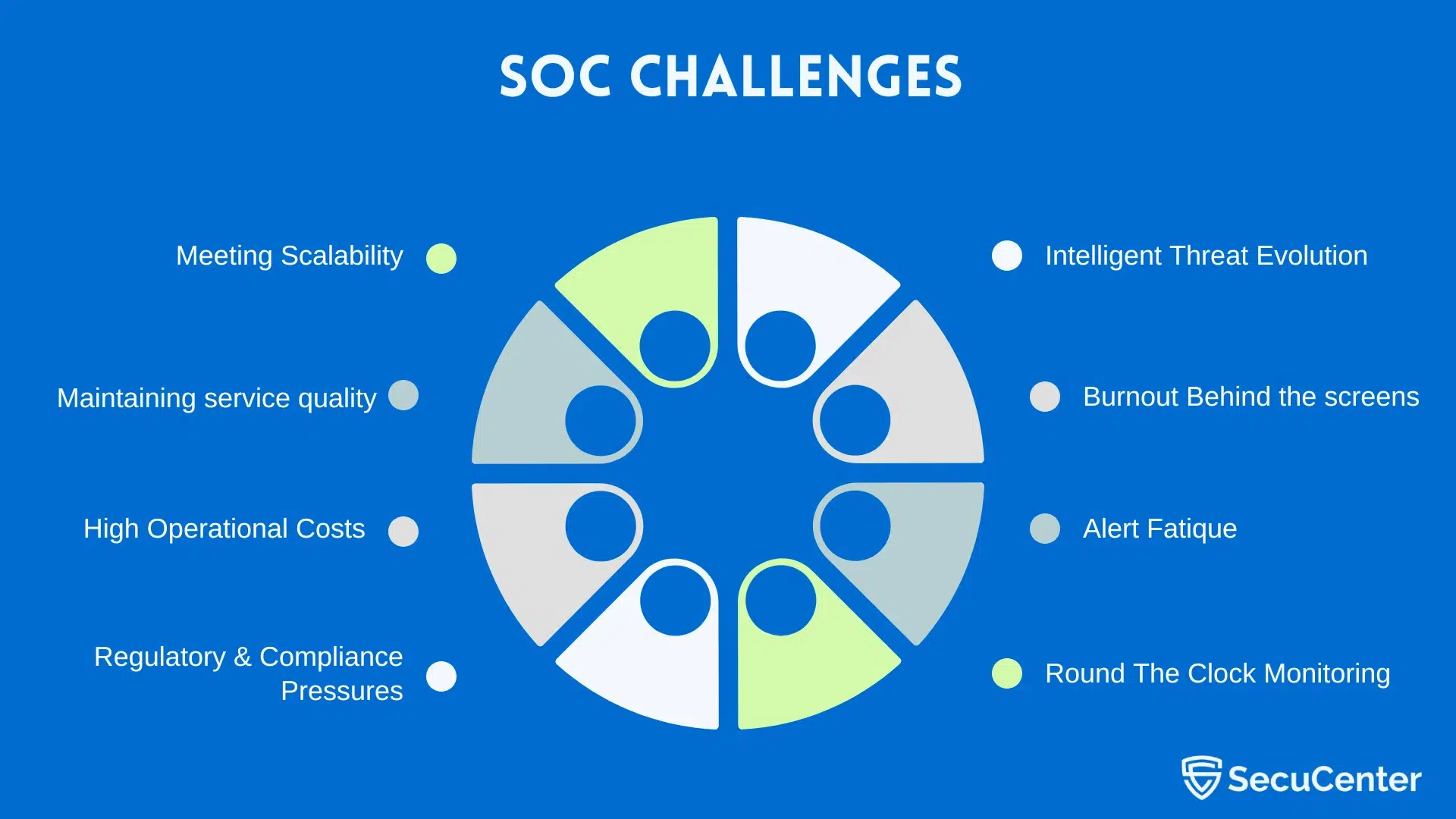
In a world where cyber threats evolve faster than ever, Managed Service Providers (MSPs) must enhance their service portfolios with white label Security Operations Center (SOC) solutions. For MSPs, implementing an AI-powered white label SOC is not just about technology — it’s about strategy, execution, and market readiness.
This detailed 30-day implementation checklist provides a step-by-step roadmap to launch your white label SOC efficiently, minimize risks, and achieve full operational readiness under your brand.
What Is a White Label SOC for MSPs?
A white label SOC allows MSPs to offer 24/7 threat detection, monitoring, and response to clients under their own brand — without building infrastructure or hiring large security teams. It’s a fully managed SOC-as-a-Service (SOCaaS) delivered by a specialized cybersecurity partner but branded as your own service.
By implementing it strategically, MSPs can expand their cybersecurity offerings, increase recurring revenue, and gain competitive advantage in a saturated market.
Why a 30-Day Implementation Plan Matters
Launching a white label SOC can seem complex — involving integration, automation, branding, client onboarding, and process alignment.
A structured 30-day plan breaks this into manageable steps, ensuring you go from concept to live operations without delays or disruptions.
30-Day White Label SOC Implementation Checklist for MSPs
Week 1: Assessment & Planning
1.Define Your SOC Objectives
Identify your core goals — whether it’s enhancing client security, expanding service offerings, or building a recurring revenue model.
Determine your target client base — SMBs, enterprise clients, or MSP sub-partners.
2.Assess Your Current Infrastructure
List existing security tools: SIEM, firewalls, endpoint security, ticketing systems, etc.
Identify integration points with your SOC provider’s platform.
Review current data flow, alert handling, and response capabilities.
3.Choose a White Label SOC Partner
Evaluate potential SOC vendors based on:
- AI and automation capabilities
- Compliance (SOC 2, ISO 27001, GDPR, HIPAA)
- Brand customization features
- Integration support (Microsoft 365, AWS, Azure, Google Cloud)
- Transparent pricing and SLAs
Select the provider that aligns best with your MSP goals and client expectations.
4.Develop a Branding Strategy
Customize the SOC dashboard, reports, and alerts with your MSP’s logo, domain, and brand colors.
Prepare branded marketing materials, brochures, and landing pages to announce your new cybersecurity offering.
Week 2: Integration & Configuration
5.Technical Environment Setup
- Connect your existing infrastructure monitoring tools and SIEM platforms with the SOC backend.
- Ensure secure data transfer using encrypted APIs or VPN tunnels.
- Configure user access roles for SOC administrators, analysts, and MSP technicians.
6.AI and Automation Configuration
Enable machine learning models for threat detection and behavior analytics.
Create automation playbooks for incident triage, alert escalation, and response.
Integrate your SOC with SOAR platforms (Security Orchestration, Automation, and Response).
7.Test Security Integrations
- Validate log ingestion from endpoints, firewalls, and servers.
- Run test incidents to verify detection, alert generation, and automated response accuracy.
- Adjust alert thresholds and correlation rules to reduce false positives.
8.Compliance and Policy Alignment
- Ensure your SOC setup adheres to GDPR, HIPAA, NIST, and ISO standards.
- Document internal and client-side data handling procedures.
- Establish incident escalation matrices and SLAs.
Week 3: Training & Pilot Testing
9.Internal Staff Training
Conduct role-based training for:
- L1/L2 SOC Analysts on alert management
- MSP Account Managers on service delivery
- Sales Teams on value propositions
- Provide access to SOC dashboards and incident reports for hands-on practice.
10.Develop Client-Facing SOPs
- Define workflows for incident reporting, escalation, and resolution.
- Draft templates for monthly security reports and incident summaries.
- Align communication processes between the SOC and client teams.
11.Run a Pilot Program
- Select 1–2 existing clients for the pilot launch.
- Monitor system performance, detection accuracy, and report clarity.
- Gather client feedback and refine processes before full-scale deployment.
12.Refine Incident Response Plans
- Establish automated and manual response steps for critical attack types (e.g., phishing, ransomware, insider threats).
- Align SOC escalation with client SLAs and communication preferences.
Week 4: Launch & Optimization
13.Finalize SOC Operations
- Ensure 24/7 monitoring, alerting, and escalation workflows are live.
- Double-check redundancy, failover systems, and backup protocols.
- Verify all branding and dashboards are client-ready.
14.Launch Marketing and Client Communication
Announce your new SOC-as-a-Service offering via:
- Website updates
- Email campaigns
- LinkedIn and press releases
- Highlight AI-powered detection, automation, and 24/7 coverage as your USP.
15.Onboard Clients
- Schedule onboarding sessions to walk clients through SOC features, dashboards, and reporting tools.
- Create a welcome kit with service details, escalation contacts, and FAQs.
16.Monitor Performance Metrics
Track key KPIs to measure success:
- Mean Time to Detect (MTTD)
- Mean Time to Respond (MTTR)
- False Positive Rate
- Client Satisfaction Scores (CSAT/NPS)
- Use AI-driven analytics to continuously improve SOC efficiency and accuracy.
17.Continuous Optimization
- Schedule bi-weekly performance reviews with your SOC partner.
- Update automation playbooks and machine learning models based on real-world incident data.
- Regularly train your internal team on emerging threats and new SOC capabilities.
- Bonus: Post-Launch Maintenance and Growth Plan
- After your initial 30 days, focus on scaling and optimization:
- Expand client onboarding through dedicated SOC marketing campaigns.
- Integrate more tools (EDR, MDR, XDR, cloud monitoring).
- Enhance reporting with data visualization and predictive threat intelligence.
- Upsell managed detection and response (MDR) for high-end clients.
- Conduct quarterly SOC reviews with your provider for performance insights.
30-Day White Label SOC Launch Timeline (Summary)
| Phase | Key Actions | Duration |
|---|---|---|
| Week 1 | Goal setting, partner selection, branding | 7 days |
| Week 2 | Integration, automation setup, compliance | 7 days |
| Week 3 | Training, pilot testing, SOP development | 7 days |
| Week 4 | Full launch, client onboarding, optimization | 7 days |
By following this 30-day implementation checklist, MSPs can successfully deploy a white label SOC that combines AI-driven threat detection, scalable automation, and brand-ready visibility. The result? A powerful new revenue stream, stronger client relationships, and the ability to deliver enterprise-grade cybersecurity without building from scratch.
As cyber threats evolve, MSPs equipped with AI-powered white label SOCs will lead the next era of intelligent managed security — setting a new benchmark in threat detection and response excellence.